- Joined
- Jan 22, 2025
- Messages
- 6,868
- Time Online
- 27d 38m
- Reputation
- 24,087
- Location
- nevsky prospect
- Guild
- .
0. the premise:
they are watching. not you or anyone else specifically, not even actively, you may not not have an agent assigned to you. still the system watches, it is a creature with a vast sensory apparatus, passively collecting every keystroke, every packet transfer, every bluetooth connection, in hopes that it might one day become useful. your phone isn't yours, your laptop has a second processor that answers directly to three letter agencies (yes really). your router sells you out before you even connect.
this isnt even paranoia, it’s all by design.
..
.
...
.
1. exhibit a: hardware betrayal:
- Intel ME / AMD PSP: hidden coprocessors functioning as backdoors with full system access and telemetry, yes even when you're computer is shut down.
- TPM, boot guard: cryptographically handcuffs your firmware. if your pc doesn't support coreboot/libreboot, it's not really yours.
- baseband processors (phones): A second OS running wide open into exploits.
solution:
- pre 2008 laptops (thinkpads, last libreboot-compatible laptops.)
- pre 2012 desktop CPU (no Intel ME / AMD PSP)
- alternatively coreboot still works on modern hardware albeit with some microcode blobs
- purism / librem / system76 / RISCV: the only "clean" modern hardware available new, but if you can't source them in person / brick and mortar stores, you can't know beyond all doubt they haven't been tampered with.
- grapheneOS pixel: least worst phone option.
B. the procurement protocol
- cash only. no receipts. no warranties.
- buy used hardware from flea markets, craigslist, etc. if you absolutely can't source the necessary hardware locally use your goody two shoes friends as a proxy to buy online, though there is always the risk of supply chain interdiction by agencies. (yes ts really happens, it's extremely targeted and unlikely they waste resources on you but nonetheless has been confirmed, filmed / documented. I've seen the evidence, they told on themselves.)
C. disassembly and testing
- inspect for tampering:
- check screws and seams. look for:
- scratches (signs of disassembly).
- mismatched screws (original vs. replaced).
- glue residue (tamper-evident seals broken).
- inspect ports and internals:
- usb/thunderbolt ports. check for tiny implants (see: NSA’s cottonmouth).
- motherboard: look up pictures / diagrams of your model and look for anomalies, reflowed solder, etc.
D. firmware and bootloader checks
- verify firmware hash, checksums, compare against known good versions (libreboot, coreboot).
- use a hardware flash programmer (CH341A) to dump and inspect.
.
..
.
...
2. the network layer:
A. ISP Tracking
- they log everything: DNS queries, IP addresses, timestamps, traffic patterns.
- solution:
- coffee shop wifi
- VPN (mullvad) or tor connected via bridges, always.
- openWRT router, with MAC randomization, unbound DNS-over-TLS.
B. wifi and bluetooth leaks:
- your phone screams volumes past networks it’s connected to, and tracks your movement via cell and MAC.
-solution:
-randomize MAC address (openWRT, linux, grapheneOS).
- power off and faraday cage your phone when not in use.
C. the cloud: a backdoor by design
- icloud, google drive scan your files before encryption.
- solution:
- avoid, use physical storage whenever possible.
- nextcloud (self-hosted)
- cryptomator: client-side encryption for cloud storage.
D. ethernet backdoors. you thought wired connections were immutable? think again.
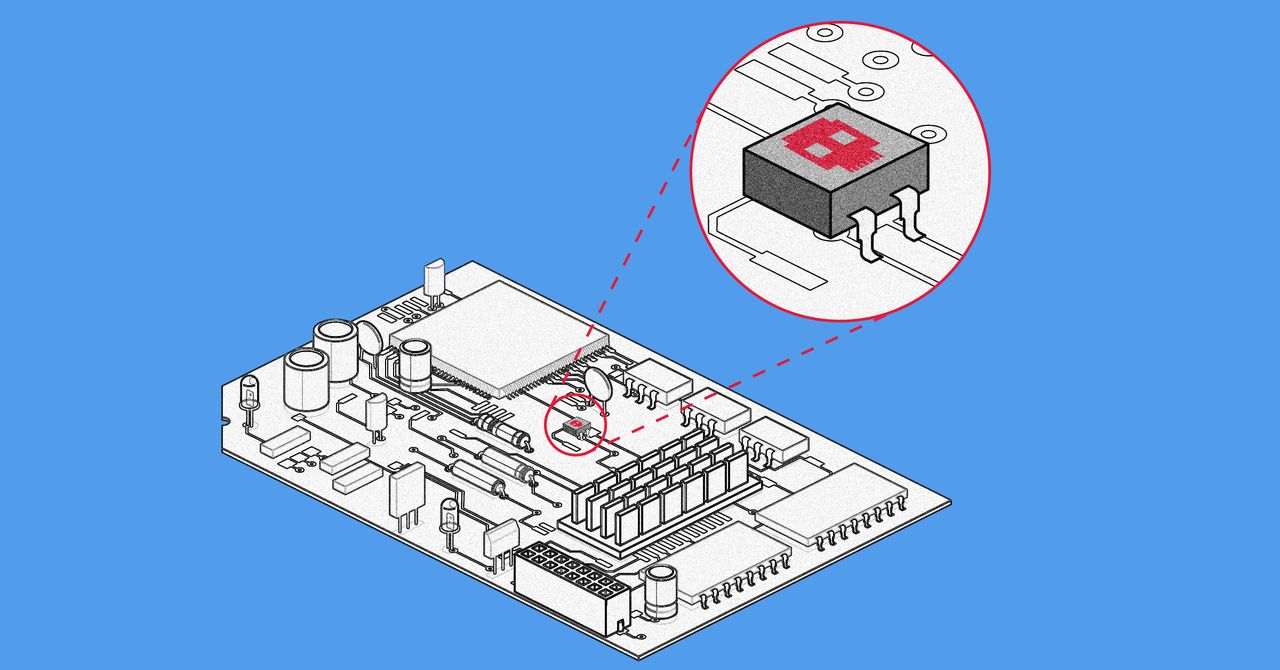
- nation-states and manufacturers implant hardware backdoors (ex; modified NICs, malicious PHY chips) and firmware exploits (Intel AMT, realtek debug modes) to intercept traffic. enterprise switches silently mirror data, while "smart" ethernet cables hide packet-sniffing microcontrollers.
detection:
- inspect NICs for extra chips/resoldering.
- dump firmware (CH341A programmer) and compare hashes.
- monitor for rogue packets (wireshark) or RF leaks (SDR).
solution:
- use open-firmware NICs (Intel 82574L).
- airgap critical machines or use fiber optics (no electrical leaks).
- encrypt traffic (MACsec, IPsec) and segment networks (VLANs).
- use shielded (STP/FTP) ethernet cables to block RF emissions. (metallic foil / braid around the wores)
E. compartmentalization:
1. airgap your most critical machine (since this will be the base of your opsec chain that you use to guarantee the legitimately of everything else) -no internet, bluetooth, ever.
...
.
.
....
3. the software dillemma :
A. telemetry is in everything
- windows 10/11, macOS, even some linux distros (ubuntu) phone home.
- solution:
- qubes OS: security through compartmentalization.
- fedora linux, minimal, no bloat.
- tailsOS: runs completely off system RAM, no persistent data stored unless set up. all network traffic routed via tor exclusively.
B. browser fingerprinting
- your fonts, screen resolution, browser, OS, GPU, etc. make you unique and identifiable
- solution:
- tor browser/firefox: resists fingerprinting (use about:config / noscript extension to kill javascript)
C. mobile apps: the worst offenders
- facebook SDK is embedded in most apps, tracking you even if you don’t use fb.
- solution:
- grapheneOS, suckless android. security through compartmentalization
- f-droid app store: open source apps only.
..
.
....
..
4. the human factor:
A. social media = surveillance opt-in
- even if you don’t post, your friends tag you. algorithms infer your habits.
- solution:
- compartmentalization, never log into anything on critical devices
- burner accounts over tor with temp emails, no personal ties.
B. smart devices
- alexa, nest, ring, smart tvs. all listen, all leak.
- solution:
- dumb appliances only. (craigslist especially useful for sourcing)
C. behavioral tracking
- unusual VPN usage? odd hours? flagged.
- solution:
- blend in. routine noise (schedule random activity in torrent client).
...
.
...
.
das eet! hit my character and time limits, hope this was informative
SOURCES:
Intel ME / AMD PSP - hidden coprocessors:
Intel ME: The most dangerous code in the world
Vulnerabilities in Intel ME allow remote access
Intel AMT “Silent Bob” exploit
NSA supply chain interdiction / hardware tampering:
NSA intercepting hardware shipments (snowden documents)
NSA hardware interdiction photo evidence:

 www.spiegel.de
www.spiegel.de
cisco confirms interception of shipments
bloomberg report on potential hardware implants
cloud surveillance and file scanning:
icloud encryption keys controlled by apple
google scans user files for policy violations
microsoft admits scanning private OneDrive files

ethernet / network Implants:
NSA’s COTTONMOUTH USB and ethernet implant
https://www.spiegel.de/media/media-35661.pdf (NSA ANT catalog PDF)
hardware implant proof of concept
 www.wired.com
www.wired.com
mobile and app tracking:
facebook SDK tracking users in other apps
android apps sharing data with facebook even if you don’t have a fb account
they are watching. not you or anyone else specifically, not even actively, you may not not have an agent assigned to you. still the system watches, it is a creature with a vast sensory apparatus, passively collecting every keystroke, every packet transfer, every bluetooth connection, in hopes that it might one day become useful. your phone isn't yours, your laptop has a second processor that answers directly to three letter agencies (yes really). your router sells you out before you even connect.
this isnt even paranoia, it’s all by design.
..
.
...
.
1. exhibit a: hardware betrayal:
- Intel ME / AMD PSP: hidden coprocessors functioning as backdoors with full system access and telemetry, yes even when you're computer is shut down.
- TPM, boot guard: cryptographically handcuffs your firmware. if your pc doesn't support coreboot/libreboot, it's not really yours.
- baseband processors (phones): A second OS running wide open into exploits.
solution:
- pre 2008 laptops (thinkpads, last libreboot-compatible laptops.)
- pre 2012 desktop CPU (no Intel ME / AMD PSP)
- alternatively coreboot still works on modern hardware albeit with some microcode blobs
- purism / librem / system76 / RISCV: the only "clean" modern hardware available new, but if you can't source them in person / brick and mortar stores, you can't know beyond all doubt they haven't been tampered with.
- grapheneOS pixel: least worst phone option.
B. the procurement protocol
- cash only. no receipts. no warranties.
- buy used hardware from flea markets, craigslist, etc. if you absolutely can't source the necessary hardware locally use your goody two shoes friends as a proxy to buy online, though there is always the risk of supply chain interdiction by agencies. (yes ts really happens, it's extremely targeted and unlikely they waste resources on you but nonetheless has been confirmed, filmed / documented. I've seen the evidence, they told on themselves.)
C. disassembly and testing
- inspect for tampering:
- check screws and seams. look for:
- scratches (signs of disassembly).
- mismatched screws (original vs. replaced).
- glue residue (tamper-evident seals broken).
- inspect ports and internals:
- usb/thunderbolt ports. check for tiny implants (see: NSA’s cottonmouth).
- motherboard: look up pictures / diagrams of your model and look for anomalies, reflowed solder, etc.
D. firmware and bootloader checks
- verify firmware hash, checksums, compare against known good versions (libreboot, coreboot).
- use a hardware flash programmer (CH341A) to dump and inspect.
.
..
.
...
2. the network layer:
A. ISP Tracking
- they log everything: DNS queries, IP addresses, timestamps, traffic patterns.
- solution:
- coffee shop wifi
- VPN (mullvad) or tor connected via bridges, always.
- openWRT router, with MAC randomization, unbound DNS-over-TLS.
B. wifi and bluetooth leaks:
- your phone screams volumes past networks it’s connected to, and tracks your movement via cell and MAC.
-solution:
-randomize MAC address (openWRT, linux, grapheneOS).
- power off and faraday cage your phone when not in use.
C. the cloud: a backdoor by design
- icloud, google drive scan your files before encryption.
- solution:
- avoid, use physical storage whenever possible.
- nextcloud (self-hosted)
- cryptomator: client-side encryption for cloud storage.
D. ethernet backdoors. you thought wired connections were immutable? think again.
- nation-states and manufacturers implant hardware backdoors (ex; modified NICs, malicious PHY chips) and firmware exploits (Intel AMT, realtek debug modes) to intercept traffic. enterprise switches silently mirror data, while "smart" ethernet cables hide packet-sniffing microcontrollers.
detection:
- inspect NICs for extra chips/resoldering.
- dump firmware (CH341A programmer) and compare hashes.
- monitor for rogue packets (wireshark) or RF leaks (SDR).
solution:
- use open-firmware NICs (Intel 82574L).
- airgap critical machines or use fiber optics (no electrical leaks).
- encrypt traffic (MACsec, IPsec) and segment networks (VLANs).
- use shielded (STP/FTP) ethernet cables to block RF emissions. (metallic foil / braid around the wores)
E. compartmentalization:
1. airgap your most critical machine (since this will be the base of your opsec chain that you use to guarantee the legitimately of everything else) -no internet, bluetooth, ever.
...
.
.
....
3. the software dillemma :
A. telemetry is in everything
- windows 10/11, macOS, even some linux distros (ubuntu) phone home.
- solution:
- qubes OS: security through compartmentalization.
- fedora linux, minimal, no bloat.
- tailsOS: runs completely off system RAM, no persistent data stored unless set up. all network traffic routed via tor exclusively.
B. browser fingerprinting
- your fonts, screen resolution, browser, OS, GPU, etc. make you unique and identifiable
- solution:
- tor browser/firefox: resists fingerprinting (use about:config / noscript extension to kill javascript)
C. mobile apps: the worst offenders
- facebook SDK is embedded in most apps, tracking you even if you don’t use fb.
- solution:
- grapheneOS, suckless android. security through compartmentalization
- f-droid app store: open source apps only.
..
.
....
..
4. the human factor:
A. social media = surveillance opt-in
- even if you don’t post, your friends tag you. algorithms infer your habits.
- solution:
- compartmentalization, never log into anything on critical devices
- burner accounts over tor with temp emails, no personal ties.
B. smart devices
- alexa, nest, ring, smart tvs. all listen, all leak.
- solution:
- dumb appliances only. (craigslist especially useful for sourcing)
C. behavioral tracking
- unusual VPN usage? odd hours? flagged.
- solution:
- blend in. routine noise (schedule random activity in torrent client).
...
.
...
.
das eet! hit my character and time limits, hope this was informative
SOURCES:
Intel ME / AMD PSP - hidden coprocessors:
Intel ME: The most dangerous code in the world
Vulnerabilities in Intel ME allow remote access
Intel AMT “Silent Bob” exploit
NSA supply chain interdiction / hardware tampering:
NSA intercepting hardware shipments (snowden documents)
NSA hardware interdiction photo evidence:

Catalog Reveals NSA Has Back Doors for Numerous Devices
After years of speculation that electronics can be accessed by intelligence agencies through a back door, an internal NSA catalog reveals that such methods already exist for numerous end-user devices.
cisco confirms interception of shipments
bloomberg report on potential hardware implants
cloud surveillance and file scanning:
icloud encryption keys controlled by apple
google scans user files for policy violations
microsoft admits scanning private OneDrive files

ethernet / network Implants:
NSA’s COTTONMOUTH USB and ethernet implant
https://www.spiegel.de/media/media-35661.pdf (NSA ANT catalog PDF)
hardware implant proof of concept

Planting Tiny Spy Chips in Hardware Can Cost as Little as $200
A new proof-of-concept hardware implant shows how easy it may be to hide malicious chips inside IT equipment.
mobile and app tracking:
facebook SDK tracking users in other apps
android apps sharing data with facebook even if you don’t have a fb account
Attachments
Last edited: